

MFA best practices you didn’t know you needed
What are the MFA best practices organisations need to consider
Its fair to say that MFA and the reasons for it is understood by most people, except maybe for artistic people who would confuse Multi Factor Authentication for Museum of Fine Arts. If you are looking for a guide on how to setup a museum, unfortunately this isn’t the right article. The aim of this guide is to provide MFA best practices that will not cost the price of a Leonardo Da Vinci painting to help implement MFA and improve the effectiveness of the solution.As a concept Multi Factor Authentication is easily understood, you really do have to have been living on a deserted island for the last twenty years not to know about the risks of using passwords. Technically MFA is not difficult often with simple solutions installed and configured in a matter of minutes. Enrolling MFA isn’t difficult either. Users can enrol a token extremely quickly and easily often in under a minute or two. It would appear on the surface that the only difficulty is choosing which Authentication Factors to use.If the need for MFA is widely understood and its not technically difficult, why is it that in companies that have implemented MFA on average have only covered just above 50% of users? Why are companies leaving the other 50% just using the very risky passwords. This article won’t go into all the reasons for this but the most common answer is that MFA is often rolled out for VPN or RDP use cases. Any reason is that often a single form of authentication is chosen and that doesn’t always work for all users.The best practice is to adopt a simple three step process, Identify, Protect and Control. Even if you have implemented MFA or just embarking on the implementation of MFA this process applies to both scenarios.- Identify is about understanding what you have and what you need. Sounds simple, but this is often where most companies go wrong.
- Protect is the implementation of the MFA solution and the rollout to the users. Yes, there will be challenges around user adoption, but get the first stage correct and adopt a couple of free simple techniques and the chances of success are hugely increased.
- Control is the final stage of acceptance that needs change and that after implementation further monitoring and adaption is required.
Identify
When someone mentions Identification, Discovery or Analysis most organisations instantly adopt a defensive pose and assume that they will need to go and buy an expensive Identity Governance or a Data Discover tool. Whilst there is no denying these will help, but this part of the process can be entirely manual. In fact, it’s not even technical it can be done by anyone with an enquiring, inquisitive mind set. Every organisation has that annoying person that keeps going “Why?”, “but what about?”, it’s that person who is best suited to do this. (If your organisation doesn’t have anyone like this then please contact SecurEnvoy, as we have a lot of employees and partners who are annoying inquisitive, who would be more than happy to help).The key to success in this stage is to adopt a simple premise – Not all users are equal. Yes that is politically incorrect in these times, but it’s not to discriminate against anyone. It’s to understand that users in your organisation have different needs. Those group of users will work in different locations, have different security needs, use different applications, using different types of devices etc.This stage is really about trying to group users based on their authentication needs, how they are going to authenticate and to what.There are several things that need to be considered.Type of Employment
Is the user a permanent employee, contractor, supplier, gig worker etc. This is important because this will dictate what an organisation will provide to these users. You are more likely to use expensive hardware tokens or provide corporate mobile phones to a permanent employee than to a third party supplier. Identifying these users will also help for the onboarding process. Not everyone is going to be onboarded with an AD account and corporate email address.Place of Work
Improving communications and unfortunate global pandemics have meant that more and more people are not always in the office. It seems to be accepted that remote working is here to stay. There is a lot of implied security with working in an office. You must get through the front door, pass the receptionist or security guard and walk to a desk. If you are not recognised at anyone of these steps you are likely to get stopped. When not in the office there is no visible check of who is logging in. To make matters more complicated, its often not a case of either or, with hybrid working people will do both. Their needs will vary day to day. Another aspect to consider is region of work. Often offices in different countries will have varying national regulations they have to adhere to.Security Level
The type and sensitivity of data that a user accesses is a vital component and does not always relate to job title. For example, a production worker may have access to personal data of a customer to check the details of a job. Often when customer data is stolen companies face huge reputational damage as it often makes headline news. The best approach is to consider all data sacred, but your most sensitive data needs extra security.Type of Devices
This is not often considered by organisations to be a differentiator, but it is when you consider why users may not adopt MFA. Many users in an organisation may not be using a corporate laptop or a corporate mobile phone. In this age of personal privacy users may not be willing to put a corporate agent or authenticator onto their personal device. This is partly the consideration of dealing where people work. It can be a little more nuanced than that, if a user already has a large number of authenticators on their device they could be prone to an attack known as authenticator fatigue. A necessary thing to think about is can a mobile device be used in all places. Is having a mobile phone allowed in your production or research area?Applications
As mentioned under security what applications and where those applications are hosted is important. Most companies do have a cloud first strategy, but will still likely have a large number of on-premise applications. Consideration has to be given to how those applications will be protected. Not all cloud authentication services can handle on-premise applications.If you do this investigation correctly you will likely find that you have around twenty different groups. If you come from a marketing background you may call these groups Personas or those from a technical background may consider these to be UML Actors. These user personas will have different authentication needs or authentication journeys.The key now is to decide which MFA Authentication Factor is best for each of those personas. A strong piece of advice it is highly likely that one factor will not be suitable for everyone.The diagram below gives some examples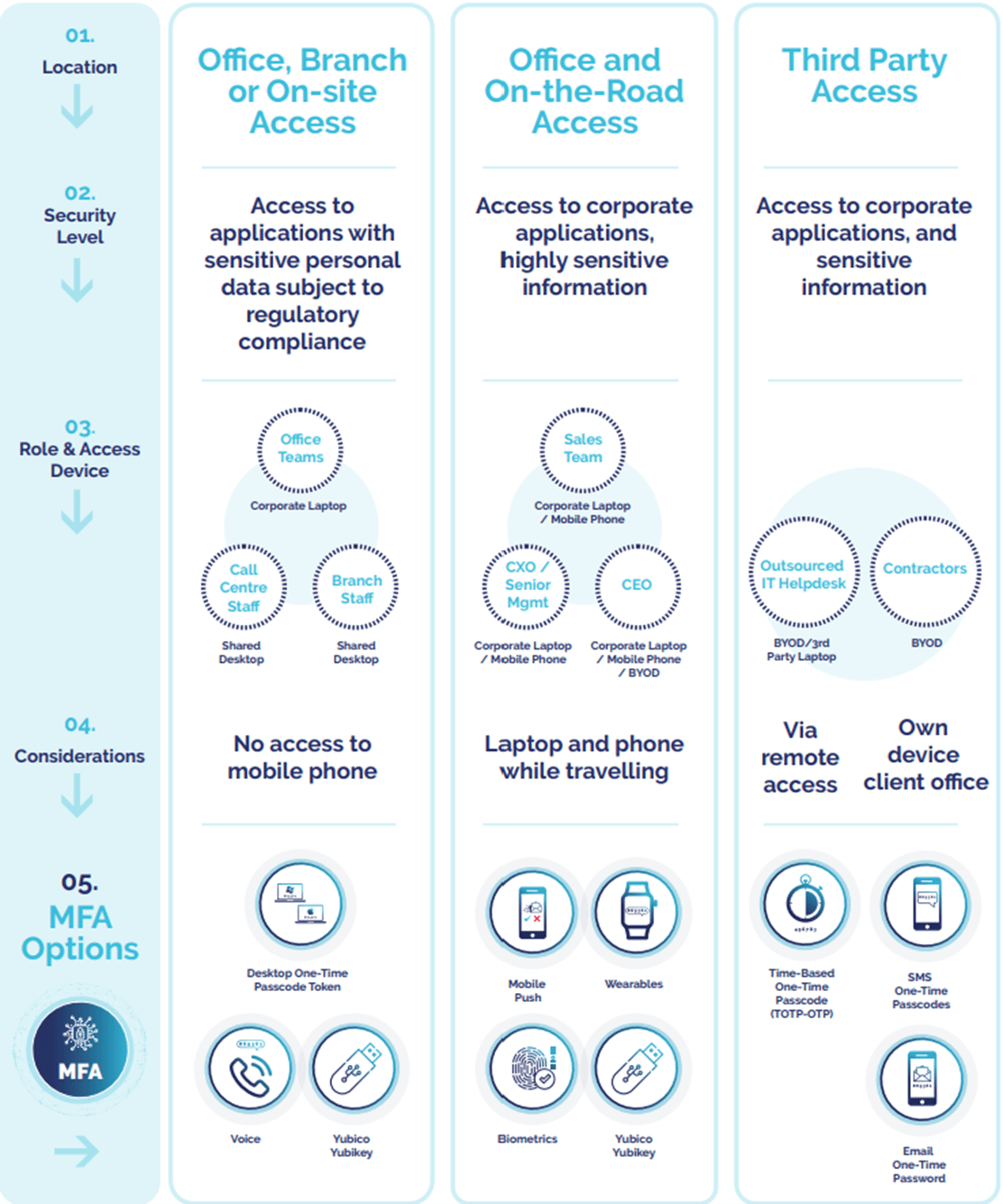 There is no right or wrong answer to which is best in every situation. Some factors are more expensive than others, some are easier to setup but may not be as secure.This is the biggest mistake companies make with MFA, it is the assumption that one size will fit all. Take the time to understand your user needs and address accordingly.
There is no right or wrong answer to which is best in every situation. Some factors are more expensive than others, some are easier to setup but may not be as secure.This is the biggest mistake companies make with MFA, it is the assumption that one size will fit all. Take the time to understand your user needs and address accordingly.Protect
Now that the users personas and authentication journeys has been mapped out, the next stage is implementing a solution to protect those users. As mentioned earlier this isn’t difficult or time consuming.Rolling out MFA to all users and all applications will ensure that users have to adopt MFA in order to gain access to their applications. In order to stop your help desk from being overwhelmed with complaints there are a couple of other things to consider that can help.Training
Unfortunately, it is human nature to resist change or to adopt anything new. Providing a simple video or guide will help show how easy it is. Explain that it is for their benefit, and it helps protect them. A useful trick and one that highlights a common frailty with passwords, is to explain that if their password is stolen at work, the hacker is likely to have access to their Facebook or Instagram account (other Social Media apps are available). Ask them to imagine the reputational damage that it could do with their friends from the bar or library.Corporate Procedures
This may seem a little draconian but it is effective. Put a small paragraph or line item in your Computer Use or Company Security Policy document mandating that MFA must be used. Also consider updating terms and conditions for external parties.Control
This final part of the process is a bit of a cheat, in that it is essentially a continuous rinse and repeat of the previous two parts. Accepting that small changes can impact the needs of users is important. Rolling out a new app, how is that going to fit in to your implementation. Opening a new office, shop etc. Are those users in those locations adequately covered. Another useful action is to ask users for their feedback. Take a select few from each persona group and periodically ask them about their experience. Make changes if required. The aim of this guide was to highlight that Implementing MFA is not a technical challenge and doesn’t require expensive complimentary tools or an overtly complicated and expensive solution.Following a simple three step process, which is largely manual, helps ensures that MFA is successfully implemented across the whole of your organisation.Published: 13 Dezember 2022
Category: Industry News, Industry Research
2FA / MFA / On-premise / Remote Working / Technology / User Experience / User Productivity
![]()
Multi-Factor
Authentication
(MFA)
Any user. Any device.
Anywhere.
For companies that take authentication seriously.
Learn more about SecurEnvoy MFA
Hear more from
our security
experts






