

How understanding your data will reduce your time to compliance (and avoid costly fines)
The Information Commissioner’s Office (ICO) handles more than 300,000 calls and receives more than 30,000 complaints each year from the general public about the privacy of their data and how it is handled by companies. ICO’s Annual Report 2021-22 shows that, on the whole, companies are taking data security and compliance seriously. But, with the risk of fines for breaches of UK GDPR and ensuring compliance with other regulations, how can you be sure that you are handling your data correctly? And even before handling your data, do you actually know what information you have and where it is stored? If a member of the public asks for their data to be deleted or access all the data you hold on them, are you ready and able to handle their request in the mandated period of time?
The data security and compliance landscape – no room for complacency
Data security and compliance is certainly not getting any easier – with the need to meet increased consumer and end-user expectations around data privacy, massive amounts of data to manage and large numbers of cyber security breaches. Ensuring that your organisation manages data security and compliance adequately is still a challenge for many organisations. Some key takeaways from 2022:
Regular data breaches – According to the latest UK government statistics: 39% of UK businesses identified a cyberattack in 2022, with 31% of businesses that reported a cyberattack estimating that they were attacked at least once per week. Fines for breaches of GDPR (and now we have UK GDPR as well as the EU GDPR) are increasing.
Changing data privacy regulations – As well as complying with existing data privacy regulations, such as GDPR, you will also need to keep an eye on any changes that might come about. The new Data Protection and Digital Information Bill, although delayed, will be going through the UK parliament and may bring with it some changes. If you are an international organisation, you may also need to adhere to EU GDPR and other regulations. Keeping up to date with the latest in data security and compliance is crucial to ensure that you can adequately meet requirements, such as data subject access requests.
Incident management plan? What plan? – In July 2022, the UK Government reported in the Cyber Security Breaches Survey 2022 that only 19% of businesses have a formal incident plan. The “biggest cyber risk is complacency, not hackers” according to the UK Information Commissioner after a construction company was fined £4.4 million as a result of not having sufficient security in place to stop a phishing email.
The simple conclusion here is “be prepared”. Be prepared for data breaches. Be prepared to respond to incidents and data subject access requests promptly. Your New Year’s (or any time of year) resolution – to understand what sensitive data your business holds, put a plan in place to manage incidents and build data management policies that will help you to safeguard your sensitive data and enable you to fulfil subject access requests quickly avoiding complaints and potential fines.
Be prepared for handling data breaches in compliance with GDPR
Under GDPR there is a duty on all organisations to report certain personal data breaches to the ICO within 72 hours of becoming aware of a breach, where feasible. If the breach is likely to adversely affect individuals’ rights and freedoms, then you also need to inform the individuals that are subject to the breach without delay.
Tools, such as SecurEnvoy Data Discovery can help before and after a breach.
Preparing for a data breach – We’ll be looking at more best practices and tips shortly but understanding where your sensitive personal data is (Step 1 in “Ensuring your business is DSAR compliance ready” below), will enable you to ensure as much data protection coverage as possible, for all your personal data.
Identify where the breach happened – After a breach, a company will typically receive a sample of breached data from the hacker to prove the breach. SecurEnvoy Data Discovery allows you to identify where that sample was accessed from and pinpoint where the breach happened. It also enables you to consider the sensitivity of the data in question in that location and help make decisions in response to the breach, including ransom requests.
Be prepared for handling data subject access requests in compliance with GDPR
DSARs or SARs – What are they?
DSAR (Data Subject Access Requests) compliance – A subject access request (SAR) is the right of individuals under GDPR to access personal data held on them and receive a copy of their personal data and other supplementary information. According to UK GDPR SAR requests need to be responded to without delay and within one month of the receipt of a request. Requests can be made verbally, in writing and via social media. Other individual rights under GDPR include the right to rectification of inaccurate personal data and the right for personal data to be erased, which also need to be responded to within one month of the request.
The top reasons for complaints to the ICO relate to the fulfilment of data access requests and providing a copy of personal data. According to ICO, information right requests are taking too long.
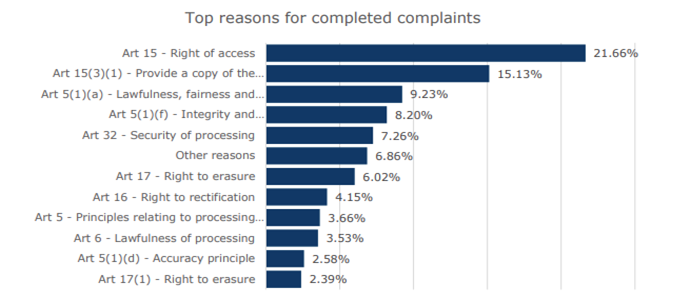
Source: Page 44 of ICO Annual report 2021-22
Ensuring your business is DSAR compliance ready
So that you can handle DSARs and other compliance requests in a timely way and avoid potential complaints and fines, here are a four key tips (and some tools) to help:
- Understand where your personal data is – Do you know where all the personal data resides across your organisation? Having personal information in specific applications is one thing, but information can be distributed across the whole organisation as unstructured data in collaboration software, for example. The first step is understanding what data you have and where it is.
SecurEnvoy Data Discovery has the ability to locate data wherever it resides across your entire digital estate, in on-premise or cloud applications, on servers and network file shares and in collaboration software. Automated search is available to help identify sensitive information such as Personally Identifiable Information (PII), Payment Card Information (PCI) health records and so on. The tool also handles bespoke rule sets and complex queries using compound search, enabling you to tailor data discovery for specific requirements. - Build policies for data management, control and access to your data. After completing step one, allowing you to understand the personal data you have, you will then be able to take that insight to tackle data management effectively and build policies and control knowing that you are making the correct decisions. You can also ensure that you give the right level of access to the data for users, employees, contractors and suppliers, using different types of MFA, for example, depending on the security levels required. SecurEnvoy MFA, for example, provides a flexible solution for a host of different secure access requirements.
- Handle DSAR compliance requests effectively
Fulfilling subject access request is a resource-hungry process and it can be a challenge locating large amounts of personal records and data held in different databases, file servers, storage and across many different endpoints.
To complete a subject access request you need to be able to extract the data and prove that you have looked for all the personal data you hold across all of your business. If you haven’t already completed steps one and two you may have difficulty responding within the one month deadline imposed by GDPR.
The beauty of SecurEnvoy Data Discovery, is that it enables you to overcome this challenge and respond to subject access requests in a quick and effective manner. You can use the pre-built searches we mentioned earlier (or build your own) to identify common personal details, such as national insurance numbers, passport and ID numbers, addresses and phone numbers and set up your SAR policy. When you receive a subject access request you can then run the SAR policy and extract the personal data, which can then be forwarded on promptly to the person requesting it. If they have asked for information to be updated, it can be carried out quickly and for the “right to be forgotten” you be able to easily identify the relevant files and data for erasure. - Keep employees vigilant of the personal data they are handling
You have now identified the sensitive personal data your organisation is holding and set up your data security and compliance policies. But how can you ensure that your data security polices are upheld and employees are aware of the sensitive data they are handling? Even with policies in place, if they are unclear, or hard to follow, employees can ignore or work around them. It is essential to have regular data security and compliance training in place to clarify policies and security processes and ensure that all staff are aware of the consequences of any data breaches.
Cyber security awareness training is a must, but you can also help to reduce the risk of data being misused by using SecurEnvoy Data Discovery to help employees understand the sensitive data they are handling. SecurEnvoy Data Discovery can be set up to alert your employees in real-time when they are storing the type of sensitive information you have identified in your policies. It can make it simple for users to remediate any data issues or handle subject access requests without the need to call on data security experts to manage every individual security alert or compliance request.
Are you ready?
Understanding the sensitive data you have and where it is in your business is the first step in building a plan, being prepared to handle data security breaches and meeting regulatory compliance requests. Using a tool, such as SecurEnvoy Data Discovery, can ease the process, of identifying personal data, helping you to build security policies and handle any data breaches and DSAR compliance requests promptly. In addition, you can ensure that data security and compliance is not put at risk owing to human error, through real-time alerts.
Discover, get set and be prepared!
Find out more about SecurEnvoy’s Data Discovery
Published: 4 März 2024
Category: Industry News, Industry Research
![]()
Data Discovery
Platform
(DD)
Data discovery across your digital estate.
Essential data discovery for any organisation.
Learn more about SecurEnvoy DD
Hear more from
our security
experts






