

What is Passwordless Authentication security and why are organisations implementing it?
Overview
With organisations actively looking at ways to improve and harden their security posture for their users, a key topic that is commonly discussed is passwordless authentication security. Many organisations are at various stages of implementing passwordless authentication for their users, with some actively adopting passwordless authentication as the default method of user authentication, all the way to some not using passwordless authentication at all.
But the clear truth behind all of this is that passwordless authentication security will replace the traditional username and password authentication method.
At SecurEnvoy, we are adapting with the latest authentication methods which provide users with more secure, but also user-friendly alternatives to using passwords.
You may be considering whether you should be using passwordless authentication and why your users might look to adopt a passwordless future?
In this blog, we’re going to explore this. We’ll look at what issues come with the traditional username and password authentication method, how passwordless authentication security works, why it benefits you and your organisation, and finally look at the backbone of passwordless authentication, using FIDO2 passwordless, Web Authentication (WebAuthn) and CTAP (Client-To-Authenticator Protocol). Grab yourself a hot drink, let’s dive in.
Issues with Passwords
It’s no secret that remembering various passwords can be a massive overhead and inconvenience to the general user, and this is of no fault of their own. A recent study has shown that the average person has 100 passwords that they’re expected to remember. Put yourself in the scenario where you’re expected to remember 100 or more unique passwords that have varying complexity requirements, such as password length, special characters, upper case letters – the list goes on!
This ultimately leads to users having password fatigue. Remembering lots of passwords from memory is generally very difficult for the average person, so what do they do to combat this? They re-use passwords, they try to use easy to guess passwords, and this leads to poor security practices.
Phishing Scams
When we get into the security vulnerabilities this can leave for the average person, a key one has to be phishing scams. Phishing scams are fraudulent attempts to trick people into providing sensitive information, such as passwords, personally identifiable information, emails and more.
You’d be part of a very small group of people if you had never seen a phishing scam from an email or a website before. The threat actor, or the individual trying to extract this information from you, will typically masquerade their intentions by using a website or email that appears to be from a legitimate source.
The main objective of phishing scams is to trick the everyday person into providing sensitive and confidential details about themselves, without revealing the threat actors’ true intentions. These types of scams can lead to numerous exploitations for individuals or business, like identity theft, personal or business financial fraud or even unauthorised access to confidential information about an individual or business.
Passwords play a key part in this, as once the target has provided their sensitive information to the threat actor, such as their password, the threat actor can then replay this on the legitimate website and gain unauthorised access to the user’s account or details. This is a primary challenge that passwordless authentication security and more importantly the FIDO Alliance are trying to tackle, and we’ll look more into this later on.
Complex Passwords vs Simple Passwords
Another vulnerability is credential brute force attacks on user credentials to gain unauthorised access to accounts. This is a big issue with users who experience password fatigue and ultimately try to use easy to remember (therefore easy to guess) passwords. Hackers will try to gain unauthorised access to user accounts by brute forcing into their accounts using commonly known passwords, or maybe even passwords that have been scraped from the user’s old accounts and listed on the dark web.
Many websites now include a password lockout policy that tries to tackle this issue. The logic of this is dependent upon the configuration, but simply put – if the user attempts to log in with the wrong credentials a certain number of times, potentially over a certain time span, then the user will be locked out. How they unlock their account is also dependent upon configuration but is typically unlocked after a certain time period, or users may be forced to reset their password.
So how do users tackle this issue? They need to use complex and hard to guess passwords. A common phrase I like to use is «Simple passwords are easy to breach, complex passwords are easy to forget». Although you are increasing your security posture by using complex passwords, you may be creating another issue by forgetting these passwords and having to reset them frequently.
Password Managers
“Password Manager enters the room.” – You’ve probably heard of password managers, we’re all prompted to use it with our web browsers, you may even be forced to use them in the workplace! Admittedly, password managers do take users to the next level with their password management and security, by also tackling the issue of having to continuously remember passwords. It’s a great tool to utilise, especially with creating complex passwords that are not easy to guess, but also not having to remember them. I’m not going to sit here and say that you should stop using password managers, because they do have their uses within the current world!
For anyone who doesn’t know what a password manager is – It is a secure and user-friendly tool that is designed to aid users in managing and storing their passwords in a secure and encrypted vault. This means that users can create passwords as strong as they desire, for their applications, and save them in a secure vault that can be accessed by the user.
The issue that comes with using a password manager is the security of accessing this password vault. Typically, this is done by using a master password that should be very secure. This should not be written down and should only be stored in your head! Most password managers also require you to change the master password after a certain period of time. How secure you make this master password is usually down to the user, but if this password can be guessed or cracked by a hacker, you can imagine the impact this will have…
The threat actor would then have access to all your application’s passwords, which is a monumental security risk. In conclusion, password managers absolutely aid users in increasing their security posture by creating complex passwords with the convenience of not having to remember them, but the security vulnerability in this comes from how you access the password manager.
We’ve now explored the downsides to using passwords and some of the security flaws that are encountered when using this traditional method of authentication. So how can you overcome this? Use passwordless authentication! Let’s look at what passwordless authentication security is and how it works.
What is passwordless authentication security?
Have you ever envisioned a world where passwords were a thing of the past? We’re not far off it! Passwordless authentication is taking over the modern security world by replacing traditional username and password authentication methods and enabling users to utilise modern authentication types to access their applications or resources, without having to use or remember passwords. Instead of applications requiring users to authenticate with a password, users can authenticate with alternative and more secure factors of authentication.
A key alternative I see is using a Push notification via an Authenticator Application installed on a mobile device, which is protected by a biometric lock. Within this authentication method there is a possession factor (something you have), being the mobile device, and an inherence factor (something you are), being a fingerprint or facial recognition.
Passwordless authentication is making it more convenient for users not to have to remember passwords and still have a secure method of authentication. Another route of passwordless authentication security is using FIDO2 passwordless solutions. Let’s look at who the FIDO alliance is and the standards that the FIDO Alliance have published.
Who is the FIDO Alliance?
FIDO stands for Fast Identity Online, and this is owned by the FIDO Alliance. The FIDO Alliance is a group of people who develop and publish technical specifications for passwordless authentication. Their mission is to reduce the world’s over-reliance on passwords, and they are doing this by creating technical specifications to meet these requirements for applications and providing easy to integrate passwordless authentication methods. The FIDO alliance has published 3 standards so far: FIDO U2F, FIDO UAF, AND FIDO2. Let’s look at what these standards are.
FIDO U2F
FIDO U2F stands for FIDO Universal 2nd Factor. It is an open standard that is developed and published by the FIDO Alliance. The aim of FIDO U2F is to provide a strong and simple second-factor authentication method. This will enhance users’ security posture allowing them to utilise a strong second-factor authentication method, but also providing a user-friendly experience. It’s important to note that FIDO U2F, is designed to be used in coalesce with the traditional username and password authentication method.
One of the key security benefits of FIDO U2F is that it relies on Public Key Cryptography. When a user registers with a compatible FIDO U2F Authenticator (such as a Yubikey), this will generate a unique key pair, which consists of a private key, that is stored on the local FIDO U2F compliant authenticator. It also creates a corresponding public key which is shared with the application or resource that is requesting the registration.
When it comes to authenticating with the FIDO U2F Authenticator, the application or resource will send an authentication request to the local FIDO U2F device that is configured. The U2F device will respond and resolve this request using the private key to sign a challenge that is sent by the application or resource. This is then verified on the application or resource side by checking against the public key. If the verification is successful, then the user can sign in securely and access their application or resource.
It’s also important to note that with FIDO U2F, the private key is only stored on the local FIDO authentication device and is never sent across the web or to the application or resource.
FIDO UAF
FIDO UAF stands for FIDO Universal Authentication Framework; you could see this as the evolution of FIDO U2F. This is yet another open standard that is developed and standardised by the FIDO Alliance. The aim of FIDO UAF is to provide a truly passwordless authentication option for users, to access their applications or resources utilising biometric or other authenticators that are FIDO Compliant.
FIDO UAF was designed to eliminate the use of traditional password authentication and allow users to login to their resources with a phishing resistant, secure, and convenient method of authentication. Like FIDO U2F, FIDO UAF also uses Public Key Cryptography. At the time of registration, the private key is stored on the local device and will never leave that device, and the corresponding public key is stored on the application or resource side.
FIDO U2F was developed to provide a strong second-factor solution for users, whereas FIDO UAF goes the extra step to remove passwords altogether and utilise the latest modern authentication options, such as biometric authentication.
FIDO2
Finally, we have FIDO2, the latest standard developed and published by the FIDO Alliance. FIDO2 encompasses the security benefits of FIDO U2F and FIDO UAF standards and builds on that. It combines the features of both standards and ultimately provides a very secure and passwordless authentication method for users to log into their applications or resources.
Once again, as we saw in FIDO U2F and UAF, FIDO2 uses Public Key Cryptography to create a key pair, the private key being stored on the local device and the public key being stored on the application or resource, to provide phishing-resistant authentication.
The FIDO2 standard is built on two core components – the Web Authentication API (also known as WebAuthn API), and the Client-To-Authenticator Protocol version 2 (also known as CTAP2). Each of these plays a key role in the FIDO2 passwordless Authentication process for registration and authentication, and we will now look at their meanings.
WebAuthn API
The Web Authentication API (also known as WebAuthn API) was developed and standardised by the World Wide Web Consortium (W3C). The W3C is a worldwide community who develops, publishes, and standardises guidelines for the World Wide Web.
Their mission is to work together for the long-term growth of the World Wide Web. The WebAuthn API is a browser-based API that allows websites to interact with compatible authenticators. Think of it as the communication and facilitation method from the application or resource wishing to set up a FIDO Authenticator to the user’s client device or browser.
This is the first step of registering and authenticating FIDO2 passwordless compliant devices. It’s worth knowing that the WebAuthn API will only work using the HTTPS (Hypertext Transfer Protocol Secure) protocol for a variety of security measures.
A key measure however is to ensure that users who are using FIDO2 Authentication are communicating with the intended website or service that they registered the FIDO2 authenticator with.
Client-To-Authenticator Protocol – What are the differences between v1 and v2?
The Client-To-Authenticator Protocol is the protocol used within the FIDO2 project to communicate between a browser or client device (such as a smartphone or Google Chrome) and a FIDO2 Compliant authenticator when registering or authenticating a FIDO2 request. CTAP is the other core component of FIDO2 passwordless Authentication. There are two versions of the CTAP Protocol, there is CTAPv1 (also known as CTAP1 or FIDO U2F) and CTAPv2 (also known as CTAP2).
CTAP1 was the first version of the CTAP Protocol. It focused on basic passwordless authentication security and supported platform authenticators (authenticators physically built into the device) and security keys such as a Yubikey. This was the protocol used for the FIDO U2F standard and is now commonly known as FIDO U2F. The issue with CTAP1 is that it had very little in the way of attestation. Attestation is the means of providing an additional inherence factor for verification. Think of it like confirming then signing for terms and conditions – you’ve confirmed you have read the terms and conditions and then have attested by signing with your own signature or a biometric.
CTAP2 was the next step on from CTAP1, and you can see this as the evolution of the protocol, it allowed users to combine factors of authentication and provided additional FIDO compatible authentication methods. CTAP2 is also built on attestation, allowing for more secure and more flexible methods for users to attest their authentication requests.
Platform Authenticators and Roaming Authenticators, what’s the difference?
Another key phrase you may have come across is Platform Authenticators and Roaming Authenticators, and you may be wondering what the difference is between both. Simply put, platform authenticators are an authentication method that is physically built into the device. This could be a smartphone or a laptop for example.
Roaming authenticators are portable devices that you can insert and use across multiple devices, you could think of them as they «roam» with you, wherever you go. This could be in the form of a USB Security Key, there are even USB-C and Lightning keys available! Or it could be an NFC card. Essentially, it’s an external authenticator that roams with you wherever you go.
There are opinions from all sides of the fence on which one is the preferred method, while platform authenticators are physically built into the device, providing added security, roaming authenticators provide convenience with more than capable security benefits. At SecurEnvoy we do not force companies into using one or the other, we provide integration options for either Platform or Roaming authenticators, or both!
How does FIDO2 provide Phishing-Resistant authentication?
Another key benefit to using a FIDO2 passwordless solution is the fact that it is considered phishing-resistant. There are numerous reasons why it is considered phishing-resistant, but I want to focus on two in this topic.
The use of public key cryptography is a key reason why FIDO2 passwordless solutions are considered Phishing Resistant, as enrolling a FIDO2 Authenticator relies on the generation of a pair of cryptographic keys. The private key is stored on the local authentication device, and the corresponding public key is stored on the application or resource. The private key never leaves the local device, it will simply sign authentication challenges sent from the application or resource.
Another benefit that makes FIDO2 Phishing Resistant is that the FIDO2 Authenticator is bound to the domain that you enrol it with, and because it is bound to this domain, it prevents credential phishing from invalid and malicious domains. For example, if you enrolled a FIDO2 Authenticator with https://securenvoy.com, the authenticator would only respond to authentication requests that come from the securenvoy.com domain.
If you tried to authenticate with an invalid or malicious domain such as https://securevnoy.com, the FIDO Authenticator would not respond to this authentication request, as it is from a different domain.
What about Passkeys?
A buzzword commonly seen right now is Passkeys. Passkeys are a form FIDO Credential that can be used across multiple devices, such as an Apple MacBook Pro and an Apple iPhone. Passkeys are built on the FIDO Standard but provide more convenience for the general user. Remember, when we mentioned how the FIDO2 Registration works, where a private key is tied to the local authentication device and does not leave that device.
Passkeys relax this requirement and focus more on the end user convenience and experience, by allowing the private key to be chained across multiple devices. Apple’s iCloud is a prime example of how passkeys are tied together across multiple devices. But this does open passkeys to interception from threat actors, as the private key can be potentially accessed if breached. Passkeys were made more for the consumer market, rather than the business or enterprise market. It benefits the consumer market for its convenience whilst still providing enhanced security over traditional username + password authentication.
With enterprises and businesses, it really depends on where they are on their passwordless journey. If they are looking to replace traditional username + passwords, then passkeys will provide additional security benefits with phishing resistance and the use of public key cryptography, which are clear security benefits over traditional username + password authentication.
How does FIDO2 Passwordless Authentication Work with SecurEnvoy?
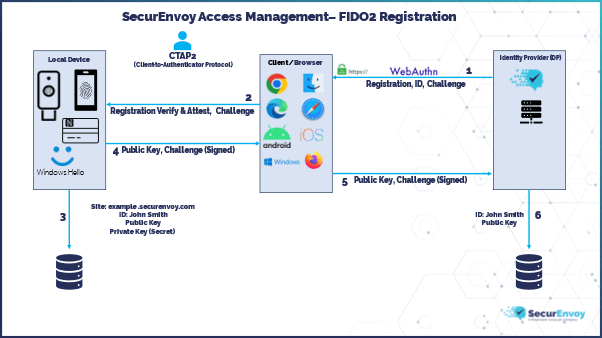
Registering a FIDO2 Authenticator with the SecurEnvoy Access Management Platform is very simple.
- A WebAuthn registration request is sent from SecurEnvoy to Client/Browser with the user identification details (username) and a registration challenge.
- The WebAuthn registration request is then verified and attested on the local FIDO2 Authenticator using the Client-To-Authenticator Protocol v2 (CTAP2).
- Once the verification and attestation is complete on the local device, data will be stored on the local FIDO2 Authenticator with the site, ID, Private Key and corresponding Public Key.
- The registration challenge is signed by the private key and is sent back to the Client/Browser along with the public key, using CTAP2.
- The client/browser now completes the WebAuthn registration request by sending the signed registration challenge along with the public key back to SecurEnvoy.
- SecurEnvoy will then store the User Identification details and Public Key on the Access Management platform, ready for user authentication.
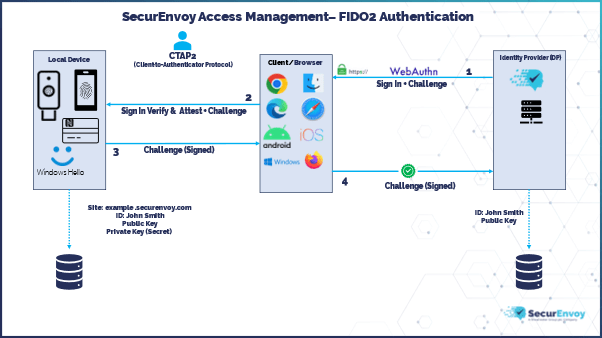
When it comes to user authentication once they have set up their FIDO2 Local Authenticator, this is very similar to the registration flow.
- A WebAuthn sign in request is sent from SecurEnvoy to Client/Browser with a sign-in challenge.
- The WebAuthn sign in request is verified and attested on the local FIDO2 Authenticator using the Client-To-Authenticator Protocol v2 (CTAP2).
- The sign in challenge is signed by the private key and is sent back to the Client/Browser, using CTAP2.
- The client/browser completes the WebAuthn sign in request by sending the signed registration challenge back to SecurEnvoy. If the signature check against the sign in challenge using the public key is OK, then the user is signed in successfully.
Make the move to Passwordless Authentication security today, with SecurEnvoy’s Access Management Platform!
I hope this blog has given you the knowledge and understanding to see why passwordless authentication security will be the future of user authentication, its benefits and how easy it is to use!
If you would like to explore this further, please don’t hesitate to contact our sales team today to discuss how SecurEnvoy can help you prepare for a passwordless future!
Published: 8 agosto 2025
Category: Industry Research, Industry News
![]()
Multi-Factor
Authentication
(MFA)
Any user. Any device.
Anywhere.
For companies that take authentication seriously.
Learn more about SecurEnvoy MFA
Hear more from
our security
experts






