

“To trust or not to trust, that is the question”
What is Zero Trust?
The fundamental belief of Zero Trust is that organisations should not automatically trust anything inside or outside the organisation’s IT boundaries, implicit trust should be removed, and use risk-appropriate explicit trust before allowing that user (or Identity) any form of access to the organisation. Zero Trust can be a bit of a misnomer because it doesn’t mean necessarily “no trust” but the basis of establishing trust first.As we’re all too familiar with today, existing IT architectures in organisations are rife with implicit trusts. Historically, architectures have been built with products and solutions that provide hardened perimeters at physical locations, that wrapped around a fleshy and chewy interior – think “prickly pear” or a “castle and moat” scenario. Zero Trust presents a change in mentality that defence shouldn’t just extend to the perimeter of our network, but also challenge what is already inside. Analysis of the most egregious security breaches shows us they were successful because after penetrating the firewalls, attackers were able to laterally move around undetected and unchallenged by exploiting implicit trusts. Therefore, implicit trusts are unsuitable for preventing modern treats, and now more than ever, especially with the change in modern working environments.The number of people working from home during 2020 doubled in the UK as a result of the pandemic. This has not suddenly caused people to become untrustworthy, it is just now their environments and equipment are not so secure. Organizations, rightly, extended their VPNs, but this created a large and easy target for attackers. The network, still supporting implicit trust, cannot adapt to the new working environment.Combine the possibility of users bringing their own unmanaged devices, and the data that the user is accessing being outside of a physical office or network perimeter, the risks associated have greatly increased. When working remotely, Users have been seen to be less security aware and more susceptible to click on suspicious links or files. According to Cyber Crime Magazine, global Ransomware damages is expected to reach $20bn by 2021!For an organisation set out to achieve Zero Trust, this will require systemically removing the existing implicit trusts within the environment. There are also challenges in changing mentalities to implementing technologies and resources. It’s not an overnight transformation and there is no single silver bullet to apply, it is as much about technology as much as business processes. Some starting points are:- Assume compromise, and the attacker is currently active.
- Use context and Identity (“Contextual Identity”) as foundation for access decisions
- Location isn’t a key trust factor, but may be one attribute to develop trust
- Encrypt your Data at rest and in transfer
- Monitor everything to identify and investigate anomalies
How can SecurEnvoy products contribute to a Zero Trust model?
SecurEnvoy offers a solution that can help build foundations of a Zero Trust architecture model.Modern Authentication
Modern authentication is the combination of access polices and MFA. SecurEnvoy introduces adaptive, conditional access to determine if access will be allowed and/or MFA enforced.Based on the signals SecurEnvoy receives, we’re able to automatically (or on a configured basis) control whether a User can access and if they’re prompted for MFA or not. Based on these signals, we’re able to verify again, before trusting. Least Privilege is also a methodology that compliments Zero Trust – that Users will only be allowed the least amount of access required to complete their task or the job at hand.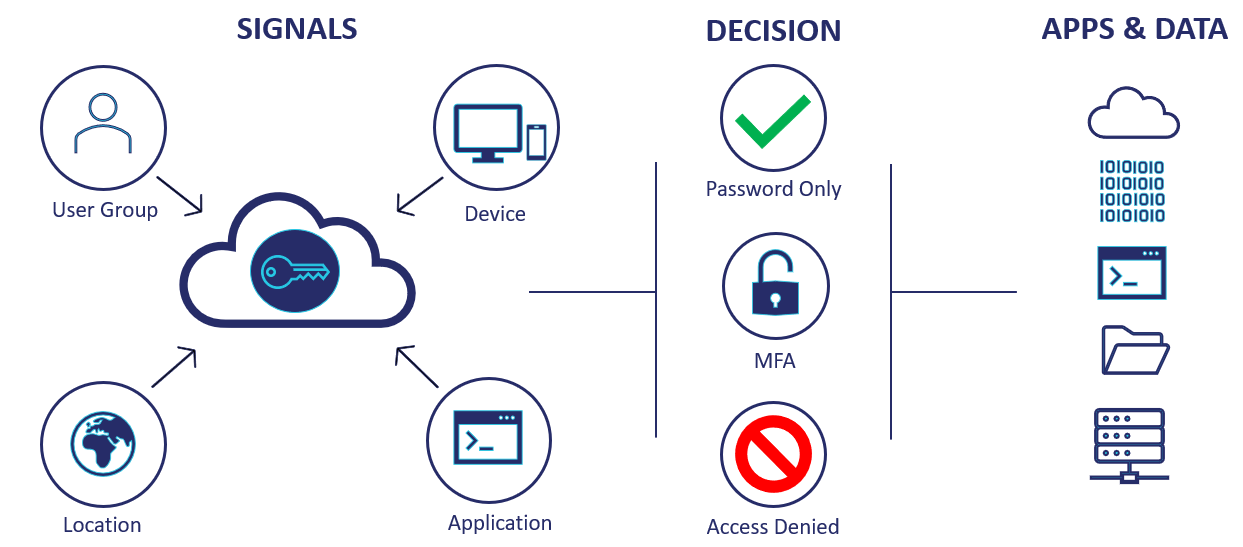 A rule-based access policy can also be configured, too:
A rule-based access policy can also be configured, too: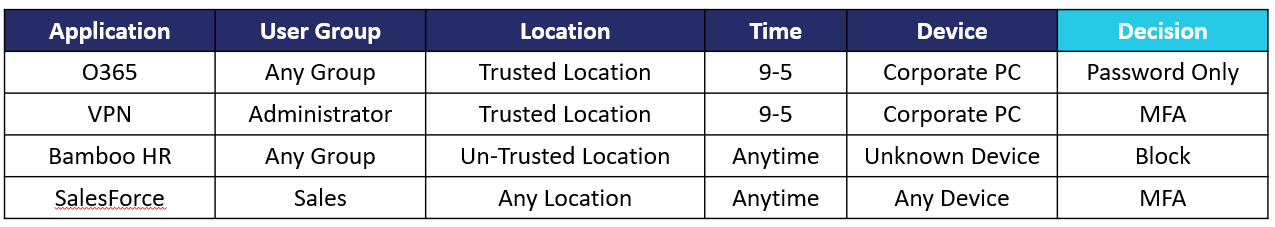 MFA responses can be delivered in real time (or preloaded) using SMS, email, PUSH or a Soft token via the SecurEnvoy Authenticator App. Also, integration with Biometrics and the use of Hardware Tokens means MFA is always available, even if the User is offline.SecurEnvoy’s MFA can also be implemented right at the very start of the User’s interaction with the environment – by applying MFA at the point of authentication into the environment with the Windows Login Agent (WLA). We can be certain that the User is who say they are by prompting the User for an MFA response. WLA can support Windows Endpoints and Servers both console and remote connections.In addition, MFA can also be applied against VPNs, IIS applications, RDS and ADFS enabled applications. This ensures that remote connectivity is secured and access to applications is protected against unauthorized access with just username and passwords. We know that username and passwords just aren’t enough anymore.
MFA responses can be delivered in real time (or preloaded) using SMS, email, PUSH or a Soft token via the SecurEnvoy Authenticator App. Also, integration with Biometrics and the use of Hardware Tokens means MFA is always available, even if the User is offline.SecurEnvoy’s MFA can also be implemented right at the very start of the User’s interaction with the environment – by applying MFA at the point of authentication into the environment with the Windows Login Agent (WLA). We can be certain that the User is who say they are by prompting the User for an MFA response. WLA can support Windows Endpoints and Servers both console and remote connections.In addition, MFA can also be applied against VPNs, IIS applications, RDS and ADFS enabled applications. This ensures that remote connectivity is secured and access to applications is protected against unauthorized access with just username and passwords. We know that username and passwords just aren’t enough anymore.Data Discovery
One of the first steps that need to be taken in the move to achieving Zero Trust and securing access with MFA is conducting a risk assessment to understand what sensitive data you have, where it is stored and who should have access to it.With the growth of different devices, and with data stored on external drives, USBs and in applications and collaboration tools, organisations are finding it increasingly difficult to keep track of their sensitive information everywhere.SecurEnvoy Data Discovery is designed to automatically discover where data resides for classification, monitoring and control. It can significantly speed up the process of detecting sensitive and confidential information across the business, whether on user devices, on-premise or in the cloud. Once discovered and classified, policies can be put in place to monitor and detect access to data as part of your Zero Trust strategy.Conclusion
To summarise, the future of work will be hybrid, so a modern working environment must be flexible and adaptive. It must support remote workers, remote data and remote applications (such as SaaS). The architecture may restrict access, but it must be flexible enough to support an increasingly interconnected business. It must adapt to the needs of the business while allowing that business to thrive despite the threats enabled by being so connected.Zero Trust supports all these goals by using context and identity as the control plane and minimizing access to the least required to do the job at hand. This allows the business to work as required, and not to be inappropriately constrained by security controls. Users can have risk-appropriate access to resources from any device, any time and any location, and with the same security controls in place regardless of the situation. It enables the secure use of cloud computing and secure access to on-premises resources and facilitates the migration from the latter to the former.Published: 13 julio 2022
Category: Industry News
![]()
Data Discovery
Platform
(DD)
Data discovery across your digital estate.
Essential data discovery for any organisation.
Learn more about SecurEnvoy DD
Hear more from
our security
experts
What to read next...







