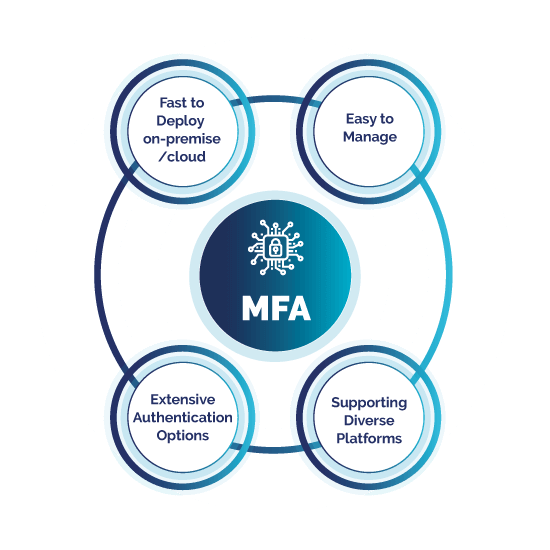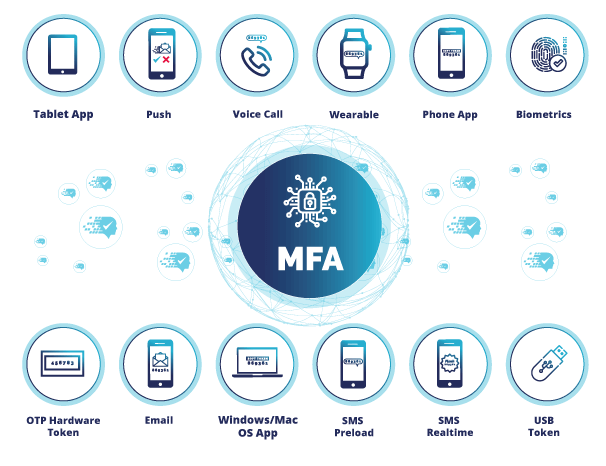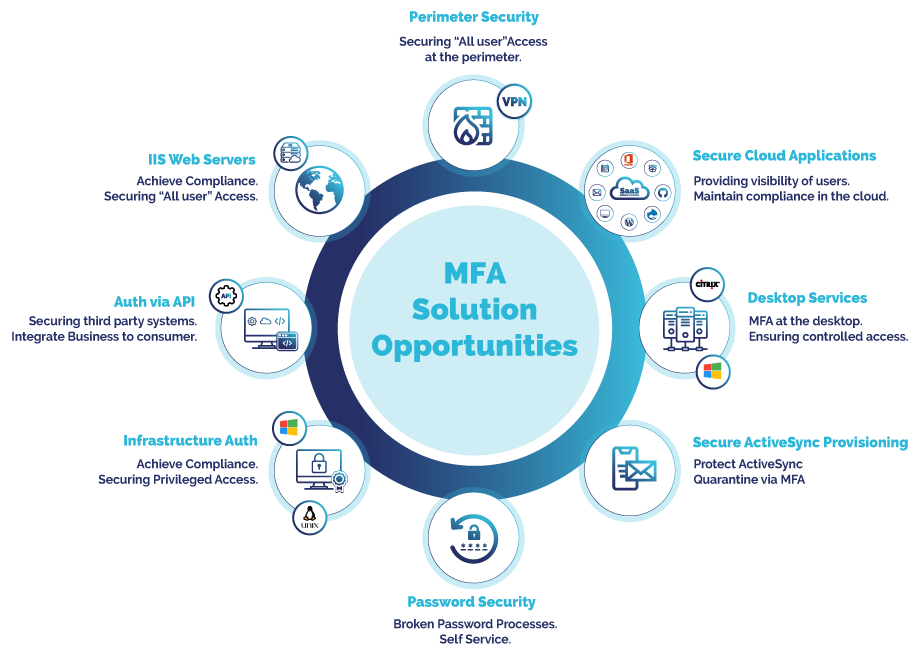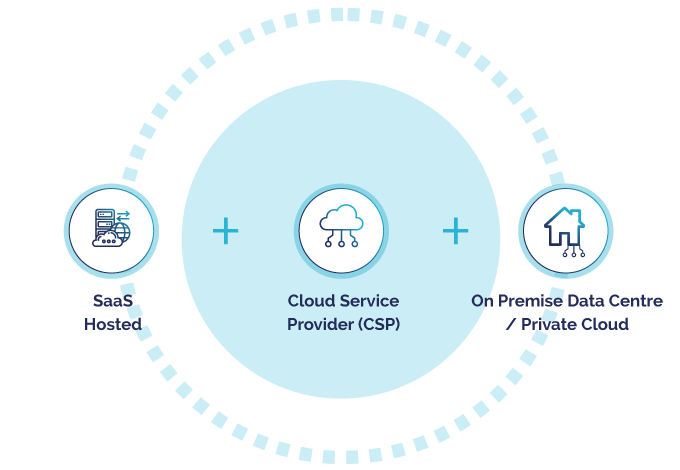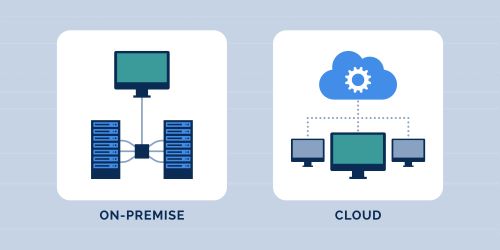
Flexible Access Management Security that allows you to select the deployment method that is right for your organisation
Choosing Control Over Cloud In today’s rapidly evolving digital era, the shift towards cloud-first strategies is unmistakable. However, amidst t...
Jordan Delany
Access Management / Cloud / On-premise